Suricata Continued - The YAML File
Continuation of the deep dive into the greatest IDS ever created
Hello frens.
I hope you did your homework! If you didn’t check out the Suricata 6.0.0 documentation (or the last stack) and go learn something useful.
If you did that, then you may have an idea of what we’ll be discussing today.
We’re going to dissect the Suricata YAML file!
There’s so much power in Suricata due to it’s vast array of features, but enabling and maximizing these depends on the configuration of the software. That’s where the YAML file comes into play.
I once documented the entire Suricata YAML file for my organization and it turned into a 20+ page document. Instead, I’m going to hit some of the highlights - enough that you can speak intelligently about it in an interview should you interview with someone who actually knows about the software.
If you want to start your cyber career in the next 8 weeks, become a paid hoodie in the stack. What are you waiting for??
Let’s do it.
If you installed Suricata with apt in the last module, you would have the following directory:
/etc/suricata/
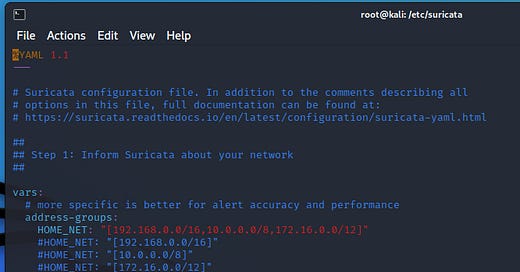
So let’s VIM suricata.yaml and see what we see:
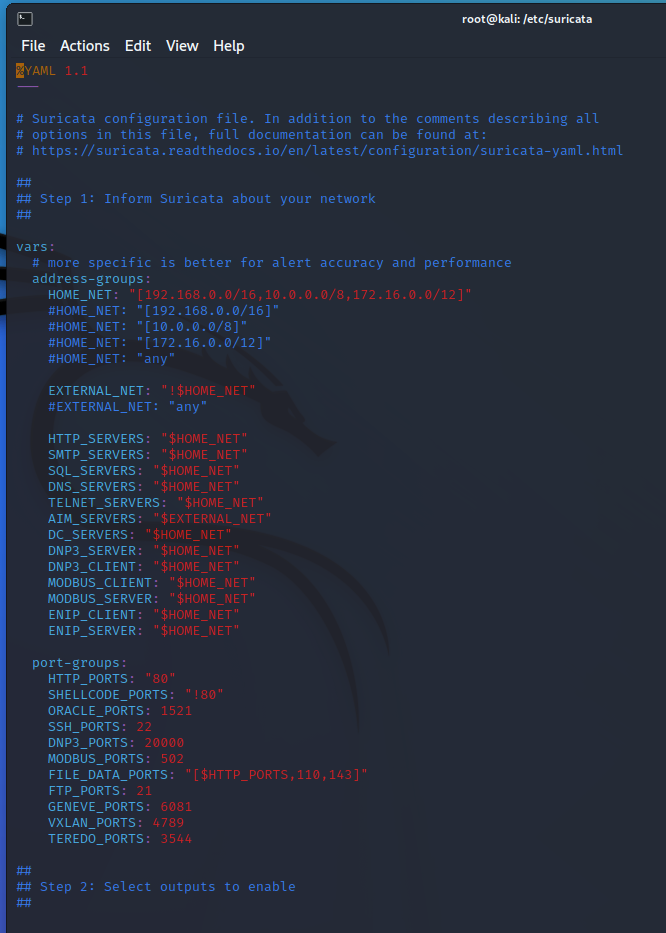
This is only the first 53 of 1900+ lines, so we’re only going to hit the highlights. Anything not explicitly mentioned should be researched before adjusting, unless it’s a test machine, in which case, you should be learning by breaking things :)
So first off, we can see the $HOME_NET and $EXTERNAL_NET variables defined. Some rules will use these variables, and to the surprise of no one, the home net variables are the RFC-1918 defined internal non-routable IP addresses. HOWEVER, this is important to note: