Hello, Hoodies!
If you want to be a great pentester, there are some non-negotiables, and Network Pentesting is one of them!
But learning metasploit is a lot like learning Python. There’s SO MUCH to learn that it doesn’t happen overnight. But we’re here to guide you through it. This is the first of many substacks on metasploit, and it’s a lot, so hold on tight.
A quick update:
The first cohort of the SOLD OUT Zero to Hoodie Cybersecurity Bootcamp is going better than I ever could have imagined.
If you want to get in on the next one (probably launching November 1st) keep your eyes peeled for a preregistration wait list dropping soon.
If you’d rather learn at your own speed for a fraction of the cost, become a PAID HOODIE in the STACK:
Back with another killer article, here’s Hoodie X to break down metasploit for you:
Hey there, Hoodies!
Earlier we learned about the burp suite tool. Which could be used for web application pentesting. But in this article, we will be seeing a tool, or more like a suite of tools, that can do anything! From information gathering to gaining access to privilege escalation to covering tracks.
This is the mighty Metasploit.
Note: To get the best out of this article, I recommend you execute all the steps with me.
What is Metasploit?
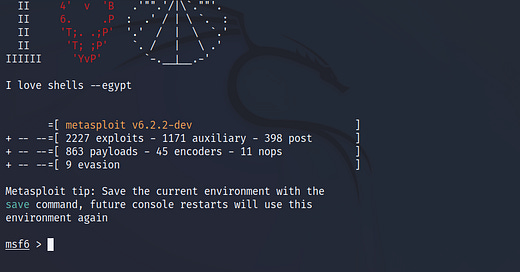
Metasploit is a penetration testing framework. It contains over 2223 exploits of all kinds of services and 1171+ auxiliary modules which are used for information gathering, scanning, and enumeration.
Not just that, Metasploit provides us with 864 payloads for different types of operating systems like Linux, Windows, macOS, Android, etc. Along with the payloads, we have 45 encoders, 11 nops, and 9 evasion methods to make a payload undetectable from antivirus solutions.
Last but not least, Metasploit provides us with over 398 post exploits, which we can use to gain more privilege over a system and much more.
Let’s see how we can install it.