Hello Hoodies.
We still have 7 seats left to the Zero to Hoodie Cybersecurity Bootcamp. You have 10 days until the first lecture. If you need direct instruction and community to succeed, sign up here. Still 40% off:
Let’s dive into the lesson!
Intruder
Now the Intruder is another wonderful feature of burp. Although it comes with limitations while using the community version.
To use the full power of Intruder you need burp suite Pro. But you can use a burp plugin to fill this need (explained later).
Now, what is the Intruder?
In simple terms, It’s a fuzzing tool. It allows us to take a request and use it as a template to send multiple requests with slightly altered values automatically like a brute-force attack.
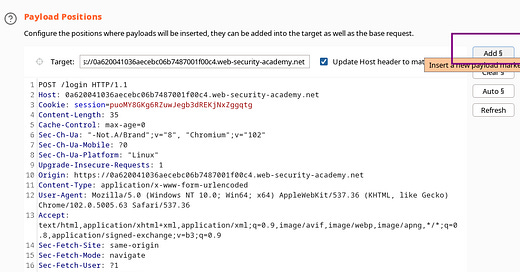
There are four sub-tabs inside the intruder. These are Positions, Payloads, Resource Pool, and then Options.
Cyber’s Note: Your version of Burp might have “Target” as your first section, which is included in the “Position” tab in future sections, explained below.
Position
It has 2 main sections. The “Choose an attack type” section is used for defining the attack types. There are 4 attack types:
Sniper
Battering ram
Pitchfork
Cluster bomb
By searching for and clicking on “sniper” you will be able to see them all and brief about why they are used. (If you don’t see the definitions on your version of Burp, you can read them here):