Hello, Hoodies!
So you want to be a hacker? Let’s show you how.
You need to know how systems work, how tools work, and how to use tools to hack the systems.
Sounds simple, and it is.
So why isn’t everyone a hacker?
Because there’s SO MUCH TO KNOW.
But the more you practice, the more you learn, and the smaller the black box of what you don’t know begins to shrink.
Which is why we’re going to SHOW you how to hack into a REAL SYSTEM using Metasploit now that we’ve already shown you how to use it (see previous articles). This is what we have done and will continue to do with all of our tools.
So if you want to learn how to hack THE RIGHT WAY, become a PAID HOODIE in the stack. Best $20/month you can spend on education, and it’s not even close:
If you want a guided approach to learning, preregister for the next Zero to Hoodie Cybersecurity Bootcamp. $10 saves your seat. Learn more here:
https://bowtiedcyber.gumroad.com/l/mpqng
Now, let’s dive in. Take it away, Hoodie X!
Hey there, Hoodies!
In the previous article, we learned about Metasploit and how to use it. And we performed all the demos with a windows machine. So, it’s time to play with a vulnerable machine(Linux). Here I will show you both approaches with Metasploit and without Metasploit. And also try to explain the scenario to you.
This article is based on a tryhackme room Daily Bugle. This room is completely free so all you need to access this room is to create an account and connect to the VPN.
That’s all, so let’s get to business!
Start the machine and wait for the IP address to show up. I recommend waiting 5 minutes, this will make sure all the service is running on the vulnerable machine.
METASPLOIT APPROACH
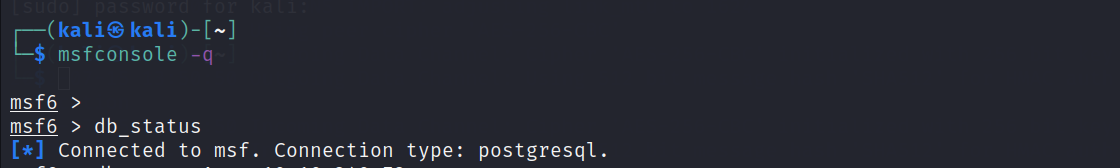
Now run Metasploit, you can run it by the 'msfconsole -q' command this will not show the ASCII art at starting.
If you don't know how to use the msf_db please look back at the previous article. For those who already followed the process.
First, run 'sudo systemctl start postgresql'. And check the database status using 'db_status'.